Trusteer recently gained access to the log files of several web servers that were hosting phishing websites. Analyzing these log files was an interesting exercise. Specifically, they provide visibility into how many users accessed the websites, when they visited them, whether they submitted their login information, and what devices they used to access the website. Here are a few interesting findings from these logs:
1) Mobile users are the first to arrive
2) Mobile users accessing phishing websites are three times more likely to submit their login info than desktop users
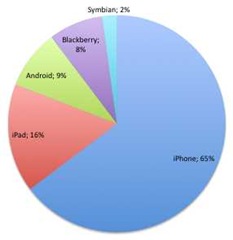
3) Eight times more iPhone users accessed these phishing websites than Blackberry users
1) Mobile users are the first to arrive
As soon as a phishing website is broadcast through fraudulent email messages the first systems to visit it are typically mobile devices.
This makes sense since mobile users are "always on" and are most likely to read email messages as soon as they arrive. Meanwhile, desktop users only read messages when they have access to their computer. Also most fraudulent emails call for immediate action. For example, they usually claim that suspicious activity has been detected in the user’s account and that immediate action is required. Most victims who fall for this ploy will visit the phishing site quickly.
The first couple of hours in a phishing attack are critical. After that many attacks are blocked by phishing filters or taken down. Hence Mobile users are more likely to be hit by Phishing just because they're "always on".
Here are some mobile user-agent fields spotted in the log files:
iPhone
Mobile Safari: Mozilla/5.0 (iPhone; U; CPU iPhone OS 4_0 like Mac OS X; en-us) AppleWebKit/532.9 (KHTML, like Gecko) Version/4.0.5 Mobile/8A293 Safari/6531.22.7
iPad
Mobile Safari: Mozilla/5.0 (iPad; U; CPU OS 3_2 like Mac OS X; en-us) AppleWebKit/531.21.10 (KHTML, like Gecko) Version/4.0.4 Mobile/7B367 Safari/531.21.10
Android
Mobile Safari: Mozilla/5.0 (Linux; U; Android 2.2; en-gb; HTC_Desire-orange-LS Build/FRF91) AppleWebKit/533.1 (KHTML, like Gecko) Version/4.0 Mobile Safari/533.1
BlackBerry
Blackberry Browser: BlackBerry8520/5.0.0.681 Profile/MIDP-2.1 Configuration/CLDC-1.1 VendorID/123
Mobile Safari: Mozilla/5.0 (BlackBerry; U; BlackBerry 9780; en-GB) AppleWebKit/534.1+ (KHTML, like Gecko) Version/6.0.0.294 Mobile Safari/534.1+
Symbian
Symbian Browser: Mozilla/5.0 (SymbianOS/9.3; Series60/3.2 NokiaE72-1/031.023; Profile/MIDP-2.1 Configuration/CLDC-1.1 ) AppleWebKit/525 (KHTML, like Gecko) Version/3.0 BrowserNG/7.2.3.1
2) Mobile users accessing phishing websites are three times more likely to submit their login info than desktop users
Most users who access phishing websites do not submit their personal information. Some submit fake information. However, compared with desktop users, mobile users are three times more likely to submit private information once they access a phishing website. Why do mobile users trust phishing websites more? One explanation could be that it's harder to spot a phishing website on a mobile device than on a computer. As a research experiment, we compared the user experience of accessing a phishing website on a Blackberry and an iPhone. Here’s what we found:
BlackBerry:
It's very difficult to tell whether an email is fraudulent since the “From” field doesn't include the sender's address but rather the name of the sender (such as ACME Bank). Some users could interpret that the device "trusts" the sender more because it is just shows the name and not the full address. Although email addresses can be spoofed, if the entire address is visible and appears “phishy”, certain users will not click through the link in the message.
In HTML mail (the most common format for fraudulent messages) when a link is embedded as a href such as <a href="http://www.acmebank.com">Click Here to Login</a> hovering over the link will not reveal the actual address. When the user clicks on the link the BlackBerry device presents the following message: "Continue to" with the real address appended. Due to the limited screen size, if the URL is long enough and well crafted (e.g. starts with www.acmebank,com.vdgrtgrt ...) it is hard to detect that the URL is not legitimate.
Once the BlackBerry switches to the browser and starts loading the phishing website the top bar shows the website name created by the fraudster (e.g. Welcome to ACME Bank) and the real address is not presented. If the phishing website is a good clone of the authentic bank’s website (and most are) there is no easy way of determining that the website is fraudulent.
iPhone:
The experience on this device is similar to the BlackBerry until the user clicks on a link. iPhone devices don't ask the user if they want to open the URL. They automatically load the page. Unlike the BlackBerry, the iPhone does have an address bar. However, due to size limitations only the beginning of the URL is shown. Here again, if the URL is well crafted (e.g. www.acmebank,com.vdgrtgrt ...) it's hard to detect that the URL is not legitimate.
Based on our findings, it is equally difficult to spot phishing websites on BlackBerry and iPhone devices.
3) Eight times more iPhone users accessed these phishing websites than Blackberry users.
According to Comscore's October 2010 U.S Mobile Subscriber Market Share (http://www.comscore.com/layout/set/popup/layout/set/popup/Press_Events/Press_Releases/2010/12/comScore_Reports_October_2010_U.S._Mobile_Subscriber_Market_Share) report BlackBerry devices (RIM) are still the market share leader in the US with almost 36% compared to iPhones (Apple) with 26%.
Then why are more iPhone users accessing phishing websites? One explanation could be that Blackberry users, many of which are issued their device by a business, are more educated about Phishing threats and thus less likely to click these links, and have better protection on their mail servers. Although we don’t have any data to validate this theory, if in fact the iPhone is more commonly used in the private sector then this is a very plausible reason for these findings. Also, the message that Blackberry devices present when a user clicks on the link in a Phishing email may discourage a certain percentage of victims from proceeding to the phishing website. Another possibility is that the Comscore market share numbers are inaccurate, and the iPhone has a greater market share than currently documented.
Recommendations:
Mobile users – never click on links in email messages, since it is difficult to determine who sent the message, what the destination address is, and what consequences may occur (phishing, malware, scam, etc.)
Banks – When customers access a web application using a mobile device, we recommend presenting them with a noticeable welcome message that reminds them to:
· Never click on links in email messages or on the web that claim to take them to the bank’s website.
· Always type the bank's address in their browser.
· Download a secure mobile browser (Trusteer offers one) that can protect them against mobile threats.
For more information see http://www.trusteer.com/blog
Source: Eskenzi PR Ltd.
This press release is presented without editing for your information only.
Full Disclosure Statement: The ICT REVIEW received no compensation for any component of this article.