Researchers from Imperva's Hacker Intelligence Initiative (HII) have found dozens of .mil, .gov and .edu web sites which have been hacked and are up for sale due to SQL injection vulnerabilities. The list includes websites government sites including Defence and State sites in the USA and Europe. Access to these sites is being sold at $55-$499 each; Noa Bar Yosef, Senior Security Strategist at Imperva provides an in-depth analysis below:
The list includes (with original hacker's typos):
The ‘traffic’ probably stands for the number of records within the Database tables. The ‘goods’ in this case are probably the needed information for the ‘Level of Control.’ For ‘full site admin’ – probably the credentials and the URL of site administrator interface.
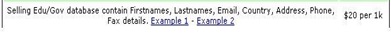
The hacker is also selling personally identifiable information (PII) from hacked sites, for $20 per 1K records:
In the screenshot below, the hacker tries to show proof of accessing the administrator interface for a major university:
The victims' vulnerabilities were probably obtained by SQL injection vulnerability automatic scanner and exploited in automatic manner, as the hacker published his methods in a post in some hacker forum – see screen shot and explanation:
In the screen shot above we can see IRC "chat" between the SQLi "master" = @evil which issues the scanning commands and the exploiting "x0wner" which performs the commands. In this specific case @evil issues command for to x0wner to obtain DB tables names ("!tbls") from vulnerable link ("www.site.gr/athlete.php?id=...") x0wner reports its findings - the tables "activities","admin",…
Imperva is the global leader in data security. With more than 1,200 direct customers and 25,000 cloud customers, Imperva’s customers include leading enterprises, government organizations, and managed service providers who rely on Imperva to prevent sensitive data theft from hackers and insiders. The award-winning Imperva SecureSphere is the only solution that delivers full activity monitoring for databases, applications and file systems. For more information, visit www.imperva.com, follow us on Twitter or visit our blog.
Source: Eskenzi PR
This press release is presented without editing for your information only.
Full Disclosure Statement: The ICT REVIEW received no compensation for any component of this article.





