by Michael Smith (Veshengro)
Denis, of Kaspersky Labs, in Moscow, wrote on December 1, 2010 that after seeing the Aurora from Moscow he decided to write about it on Twitter and then decided to search for “северное сияние” (Aurora in Russian) to see if others have noticed it too.
He then saw a number of tweets from people in Moscow who also had seen the Aurora. He then noticed "Morgan Freeman" listed in the Twitter Trends.
Thinking that something had happened to him Denis checked the tag and found a number of suspicious messages. After checking the URL he found they were malicious – a new attack being carried through Twitter at that very moment, live.
Further investigation revealed several trending topics –‘Morgan Freeman’, ‘Advent Calendar’, ‘Pastor Maldonado’, ‘Toivonen’, ‘Grinch’ and ‘Hannukah’ – with various messages with the shortened URLs. Various shortening services were used: tinyurl.com, urlcut.com, bit.ly, doiop.com, tiny.cc, alturl.com, shortlinks.co.uk, yep.it – all pointing to malicious websites.
All these links lead to br********.com/about.html which will redirect user to bestivideos****.it. Then user will be redirected to myb****.com/flash/ where user will see the following ‘offer’:
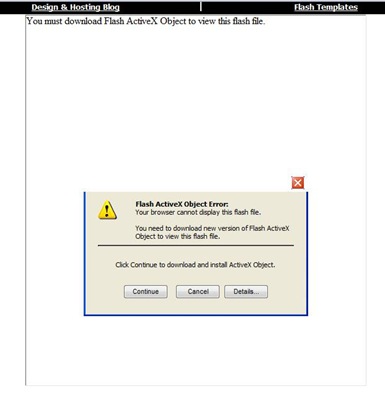
Be careful with twitter trends because popular topics could always lead to malicious messages!
It would very much appear that shortened URLs are being used to offload malware on unsuspecting users of Twitter (and other social media sites) and, maybe, a way must be found to preview the links, as full URLs, so that users can see where the link actually sends them to.
Byt.ly and tinyurl.com will, in TweetDeck always, it would appear, present a box where the real URL is shown.
If you are using Firefox then by hovering over the link the full URL is being shown and it should become practice for all of us to use browsers such like that and protection plug-ins and ensure that we see the proper web address before we click on any link.
Cyber criminals have been using the hunger of people for news about this or that for some time already and emails were being sent about before with messages about the war in Afghanistan, supposed earthquakes, and other disasters. Or messages that this or that celebrity had appeared nude, etc.
The desire by users to be the first to learn about such issues tend to be their downfall and they end up getting trapped and it proves, time and again, that computer users must become much more savvy and by now, one would have hoped, that that would be the case already. Alas, however, it is not.
It is the same with people who believe that their anti-virus software makes their computer slow and that by disabling or even uninstalling it they would have a faster computer. That is as dangerous as removing a child stair gate just because we have to step over it.
Cyberspace is a dangerous place, unfortunately, and we need to keep out wits about us when venturing there. That does not mean that we should abandon it. Just using proper commonsense and care, plus some good protection software, a safe browser and not opening links in emails that we are not sure about, and especially NOT in any unsolicited emails.
Be careful, its a jungle out there.
© 2010